Trezor Login: A Secure Gateway to Your Cryptocurrency Wallet
In the evolving landscape of digital currencies, security remains paramount. Trezor, a pioneer in hardware wallets, has established itself as a trusted solution for safely storing cryptocurrencies. One critical aspect of using a Trezor device is the Trezor login process, which enables users to access their crypto assets securely and efficiently. This article delves into the nuances of Trezor login, highlighting its importance, procedure, and security features to ensure a seamless user experience.
Understanding Trezor and Its Importance
Trezor is a hardware wallet designed to protect your private keys offline, away from potential online threats. Unlike software wallets that are vulnerable to hacking or phishing attacks, Trezor devices offer an additional layer of security by keeping the critical information on a physical device. Logging into your Trezor wallet is not just about convenience but about ensuring your digital assets remain under your control and protected from unauthorized access.
The Trezor Login Process Explained
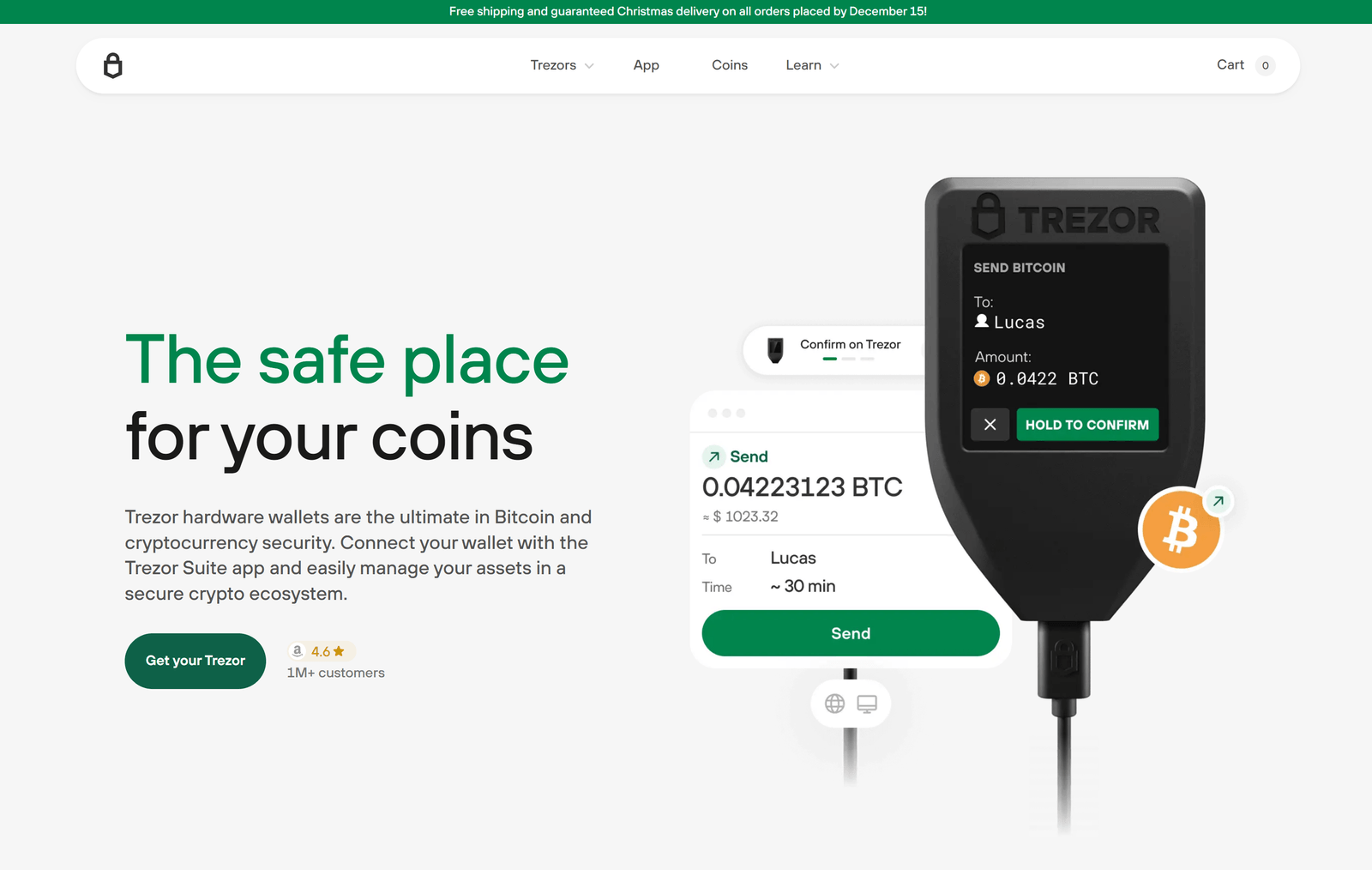
Logging into a Trezor wallet involves connecting your Trezor device to a computer or mobile device and accessing it via the official Trezor Suite or supported third-party wallets. The process begins by plugging the hardware wallet into your device through a USB connection or via Bluetooth in newer models.
Once connected, users must authenticate themselves using a PIN, a crucial security measure that prevents unauthorized physical access to the device. This PIN is set during the initial setup and is never stored on the device or online, making brute force attempts extremely difficult.
After PIN verification, users may also need to input a passphrase if they have enabled this additional security feature. The passphrase acts as a “25th seed word,” creating a unique wallet variant that only the user knows. This layered authentication ensures that even if the device is lost or stolen, the assets remain inaccessible without the PIN and passphrase.
Security Features Enhancing Trezor Login
Trezor login is fortified by multiple security mechanisms:
- PIN Code Protection: Each login requires the entry of a PIN, preventing unauthorized users from accessing the wallet.
- Passphrase Option: Adds an extra layer of security, creating a hidden wallet accessible only with the passphrase.
- Device Verification: The device itself shows the transaction details and login confirmations, so malware on your computer cannot manipulate or intercept sensitive operations.
- Firmware Integrity: Trezor devices regularly update their firmware, ensuring they stay resilient against emerging security threats.
Best Practices for a Safe Trezor Login
To maximize security during the Trezor login process, users should adhere to these best practices:
- Always download Trezor Suite from the official website to avoid counterfeit software.
- Regularly update your Trezor device firmware.
- Never share your PIN or passphrase with anyone.
- Use strong, unique passphrases and avoid simple or guessable codes.
- Disconnect the device when not in use to prevent unauthorized physical access.
Conclusion
The Trezor login process is a cornerstone of cryptocurrency security, combining hardware protection with robust authentication protocols. By understanding the steps and security features involved, users can confidently safeguard their digital wealth against online threats. As cryptocurrencies continue to gain mainstream acceptance, mastering the Trezor login is essential for anyone serious about protecting their assets in the digital age.
Made in Typedream